nmap

What is nmap?
In this post, we will focus on the network scanner "nmap". Nmap is an abbreviation for “Network Mapper”, which is an open-source tool for network exploration and security auditing.
What can it do?
By scanning the network, we can find information on what hosts are available on the network, what services they are offering, which operating system is being used as well as details about the firewall, packet filters and much more. The command uses IP packets to identify every device connected to a network, spilling out all the information mentioned above.
This means that it displays:
- Every active IP address
- The entire network
- Live hosts
- Open ports
- Vulnerabilities
- Operation Systems of devices
Originally, nmap was designed for big networks within big, so it can give a clear overview of all the devices connected to the network. With the rise in technology, this tool has been used more frequently, even by smaller businesses. Since nmap is an open-source tool and everyone can use it, regardless of their intentions, you can imagine that this challenges security measures for the company's networks.
On the other hand, nmap is not just used for malicious activities, but it is mainly used for companies to:
- Secure audits
- Audit network traffic
- Routine tasks, such as network inventory
- Managing service upgrade schedules
- Monitoring host or service uptime
- Monitor internal traffic
How to use nmap?
Syntax
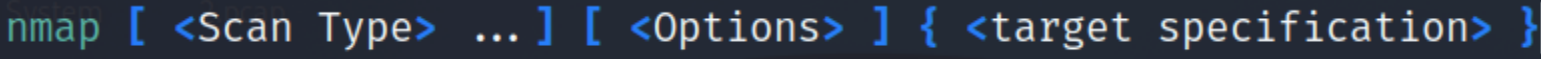
Target can be an IP address, multiple IP addresses, CIDR, or a custom range.
Port states:
- open
- closed
- filtered
- unfiltered
- open|filtered
- closed|filtered
Basic Usage
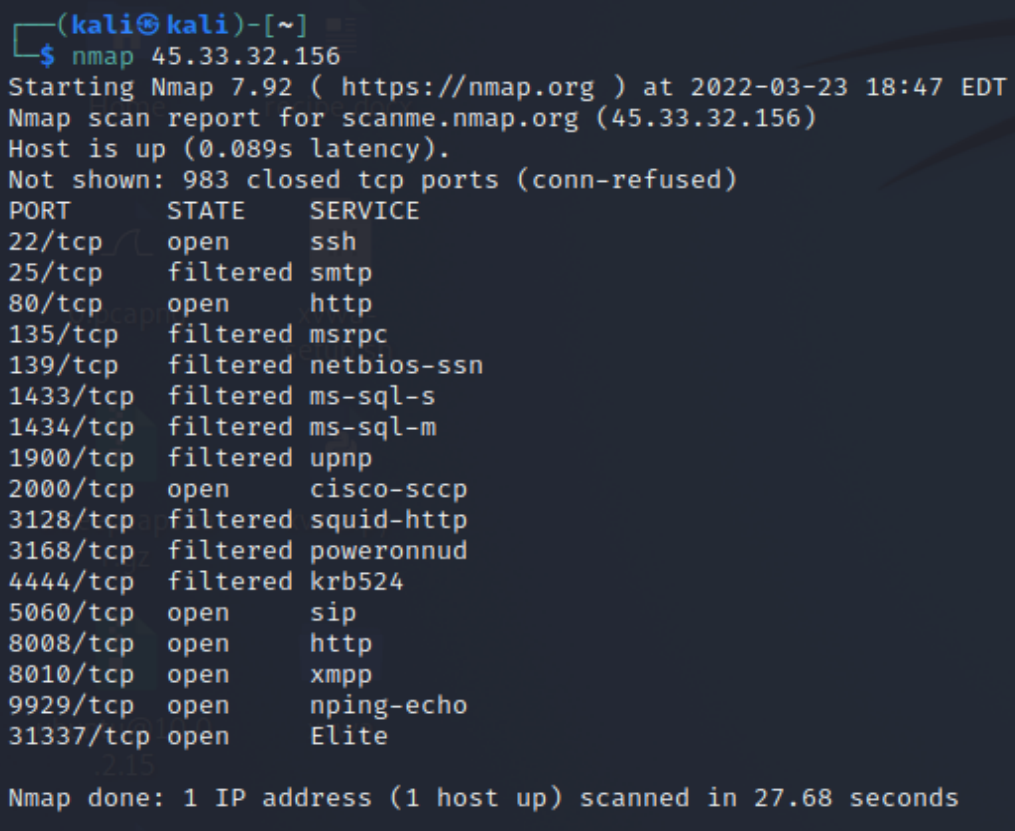
Host Scanning
nmap -sP <target IP range>
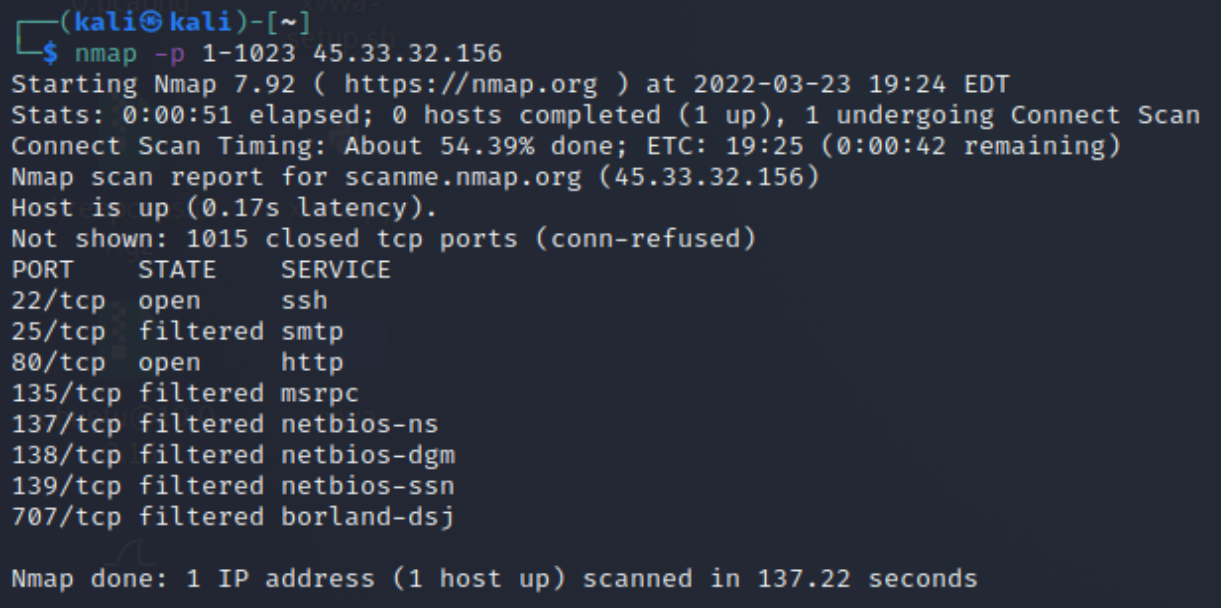
Port Selection
Select the range of ports you want to address. In this example, we are selecting ports 1 to 1023. In total, there exist 65,535 ports.
TCP/UDP Selection
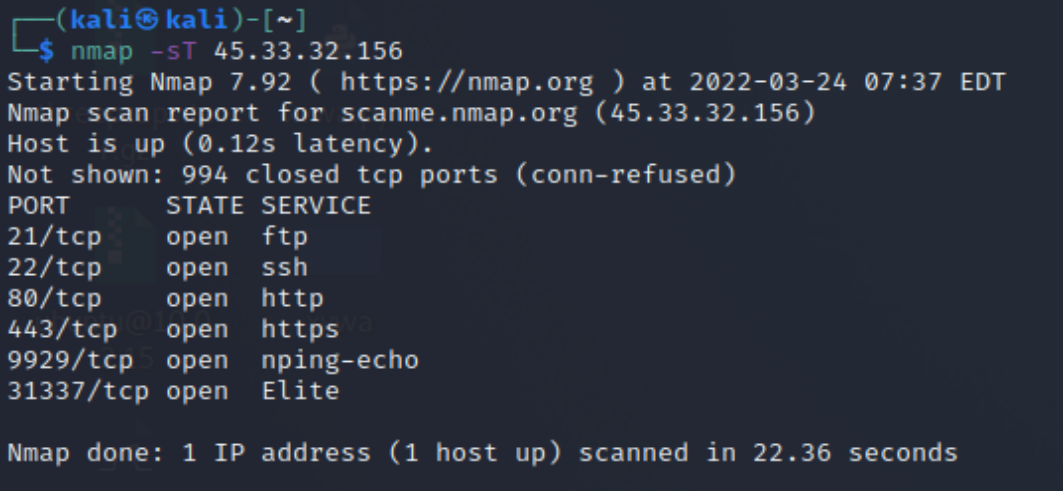
By using the command -sT you focus only on TCP ports.
Host Discovery
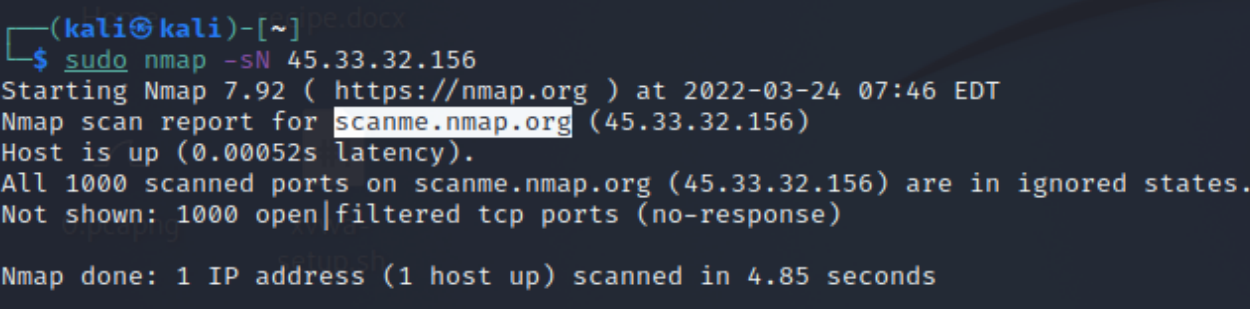
The picture below shows a host discovery without port scan, using the command -sn. This command is also known for Ping Scanning.
Output to File
Very helpful if you want to clear the screen and don’t want your results to get erased. Simply, use the following techniques to output the acquired data in the according format:
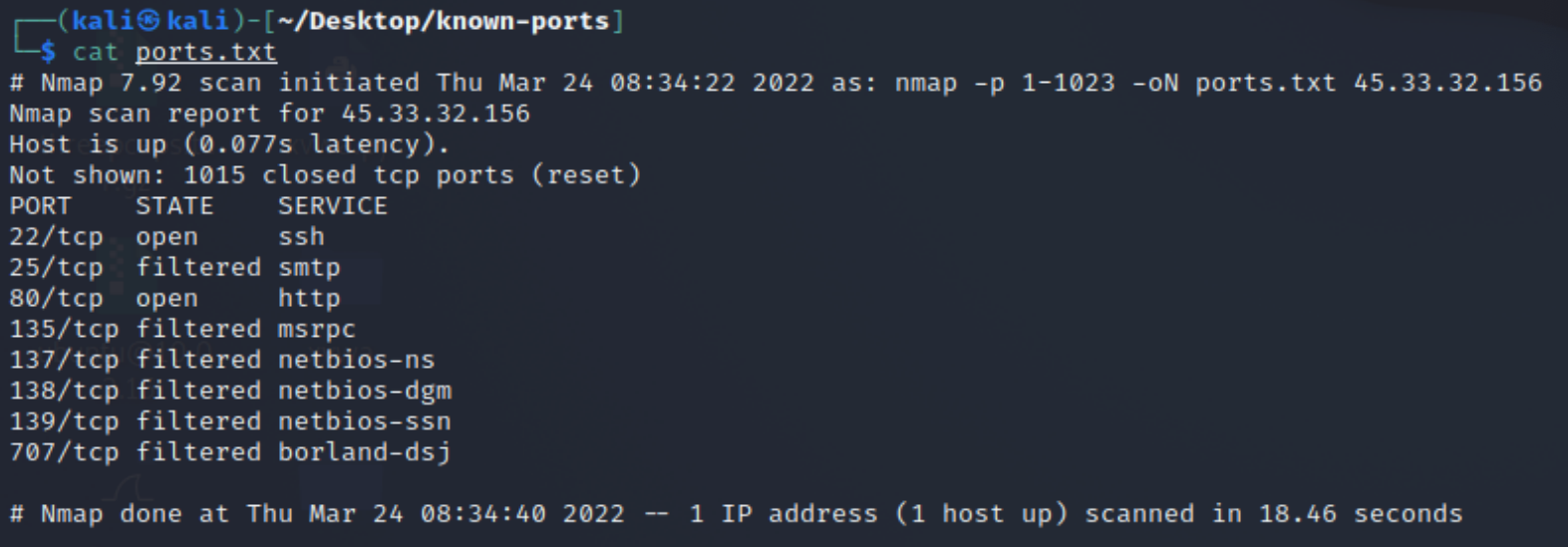
- -oN Output scan in normal txt
- -oX Output in XML
- -oS s|<kIpt kIddi3
- -oG Grepable format
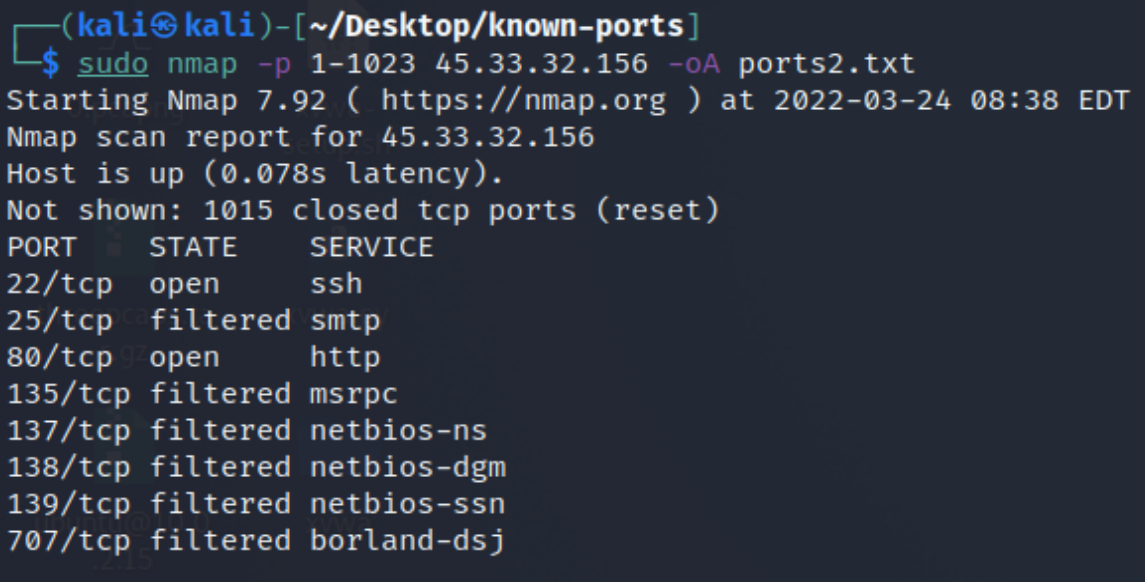
- -oA Normal, XML, and Grepable
Let's try some of the techniques mentioned above:
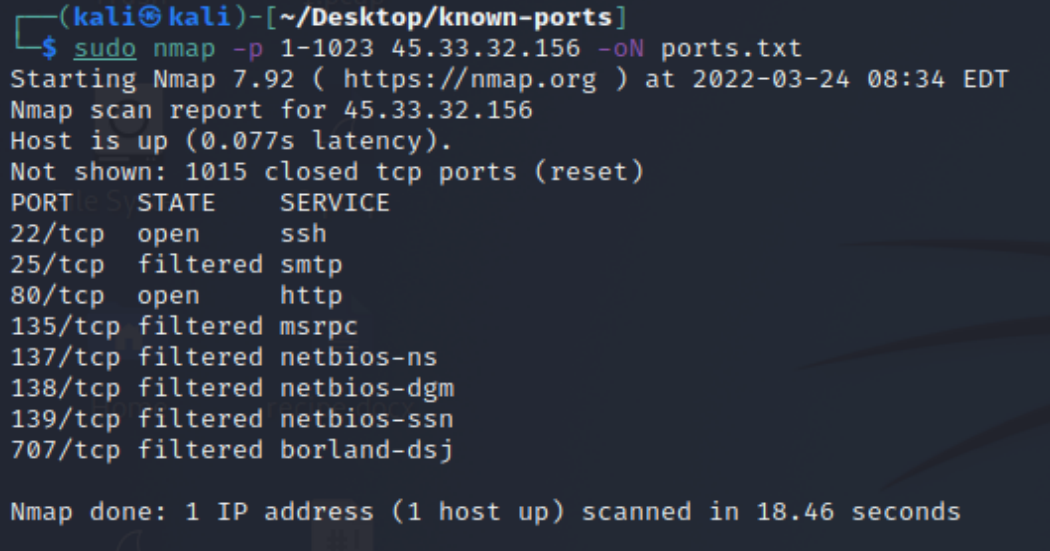
-oN
-oA
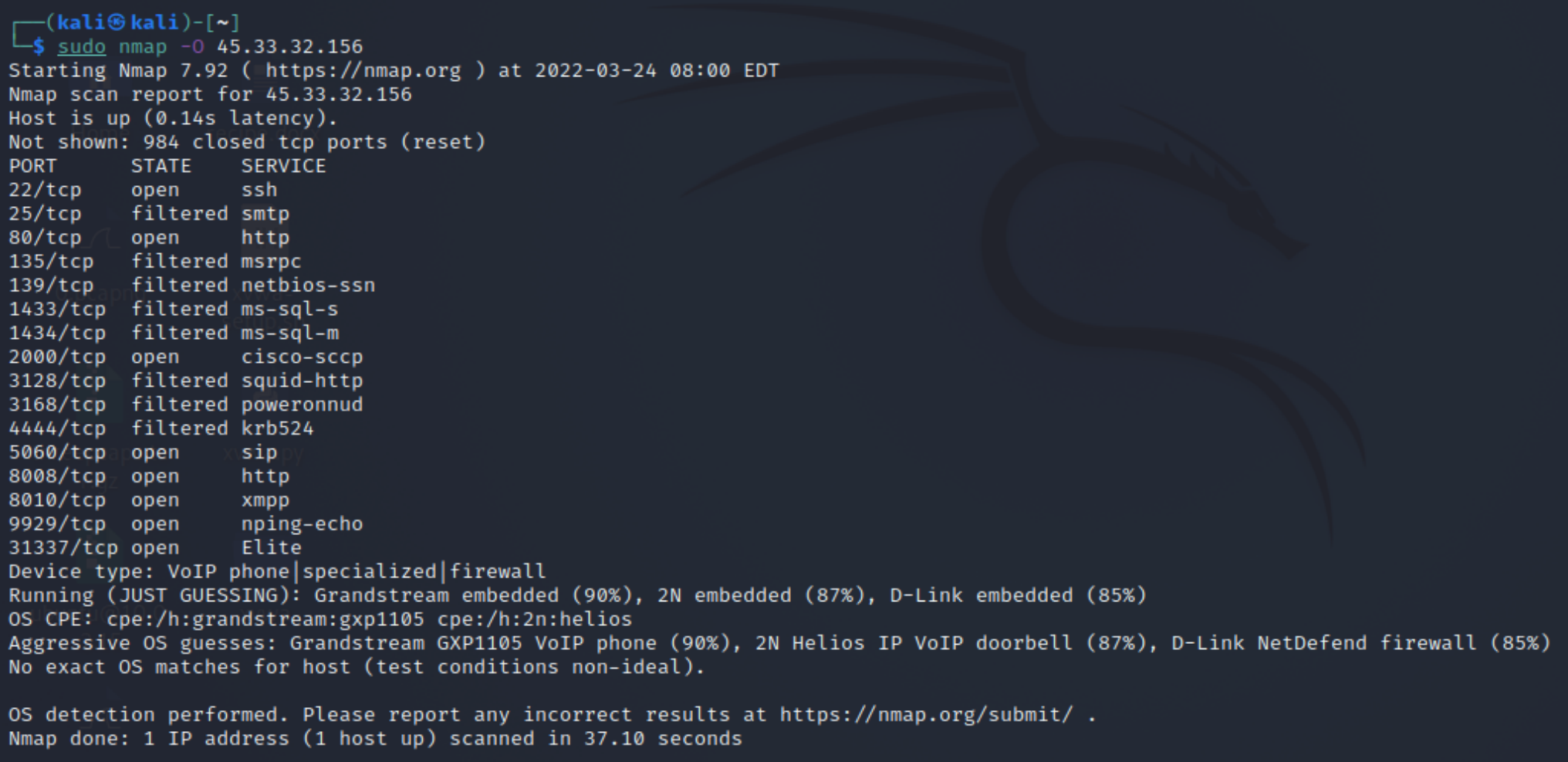
OS Detection
Nmap will figure out what OS its target is running Nmap by sending TCP and UDP packets to a particular port and then analyze its response.
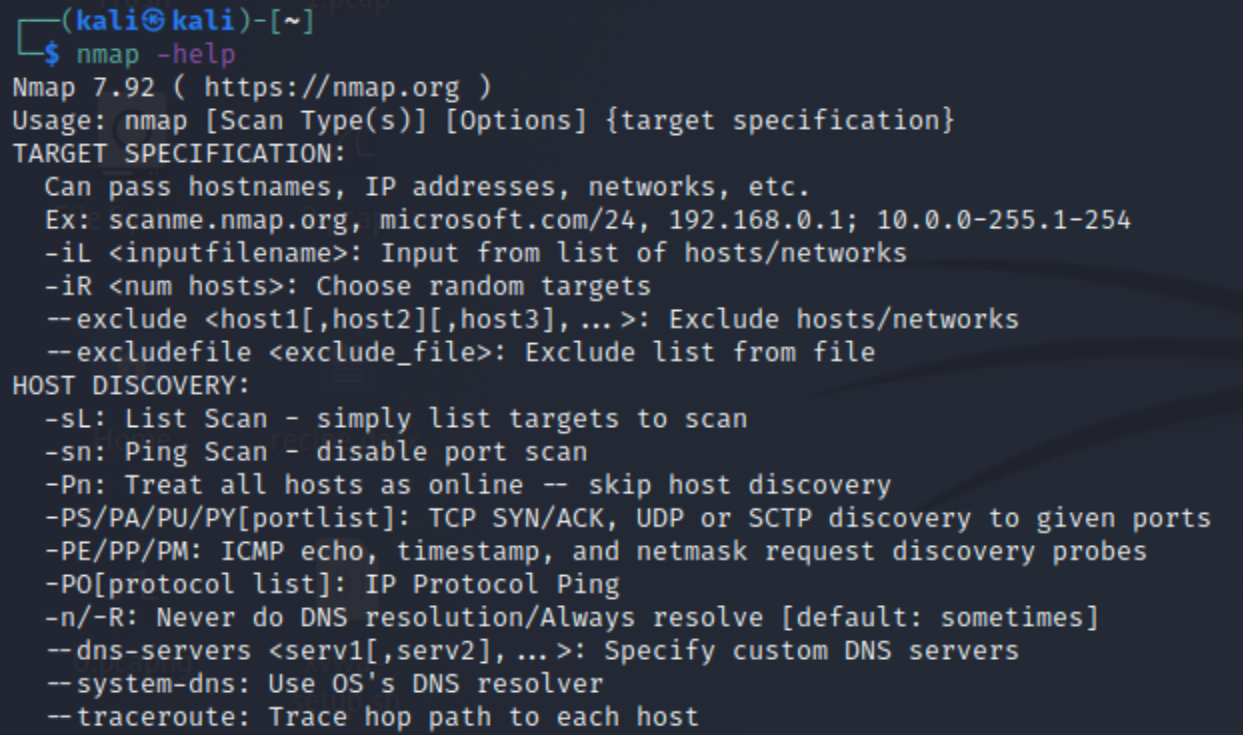
Additional information - Help Command
In order to get to know nmap better, you can simply use the help command, which shows you all the different scan types and techniques.