Evil Twins and more

In this post, I will explain 5 terms that you have probably come across or you most definitely will come across on your early cyber journey. This is a list of terms that I didn't properly understand at first, which is why it makes sense to try to explain it to someone else. Therefore, I find it more helpful if they can be explained properly so you won't struggle when you take your Security+ certification. This is the first of the many blog posts, where I will explain 5 terms, or should I rather call them to attack methods, that hackers use. Let's dive into it!
SSL Stripping
For most attackers, it is well known that communication happens through an encrypted channel, such as HTTPS. However, they can modify the path which the data is going through, so that the communication is not secure anymore. This is also called HTTPS downgrade. While you think the connection between you and the server is trouble-free, the attacker sits in the middle of your communication path, receiving all of your transferred data. This can be done in several ways such as ARP spoofing, a rogue Wifi hotspot, or a modified proxy server. Most likely, you will not even know what happens, since everything looks as usual and there will be no visual signals that will make you realize what's happening. This makes it even scarier, you have no idea that all of your data is secretly received by an unknown entity.
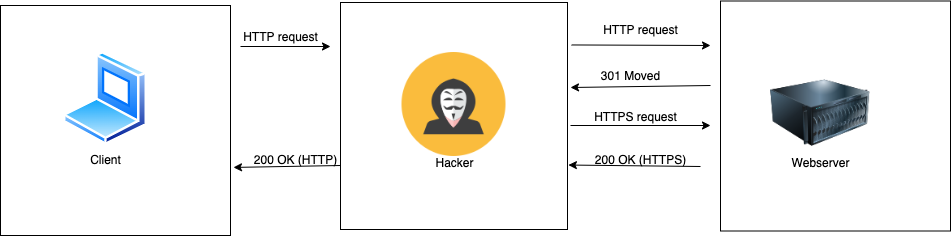
Again, you as the website visitor, send an HTTP URL to the web server, in the meantime the attacker gets this request and forwards the HTTP request to the server. After evaluating the HTTP request, the server sends an HTTPS request back to the client since it's more secure, but the hacker doesn't want that. Since the attacker is receiving the request from the server before the client does, he intercepts the HTTPS request and sends this request back to the web server. Now, the hacker successfully established an HTTPS connection to the webserver. Remember, the connection between the hacker and the webserver is encrypted, but not between you (the client) and the webserver. The attacker receives the encrypted version of the data from the server and decrypts it, after that he forwards the data over the HTTP channel to the client, without anyone knowing what s going on. This process can keep on going, and what is dangerous here, is that the client can send his credentials to the webserver, because he needs to log in to his account, not being aware that he is sending them to the hacker. This is also called an On-Path attack.
I created a visualization in order to get a proper picture of what I was describing.
Cross-Site Scripting
XSS, also called Cross-Site Scripting, is a web application development vulnerability. Here, attackers exploit the trust a user has for a website. This allows someone to run scripts within the user input fields, such as a search box for example. The way an attacker takes advantage is by inserting his code into the website and then getting the user to click a specific kind of link to start the cross-site scripting attack. After the victim clicks the link, the content of the malicious scripts runs on the victim's machine which can ultimately lead to sensitive information, such as credentials, session IDs, or cookies, being sent to the attacker.
Rogue Access Points - Evil Twins
This is an AP that has been added to your network without your knowledge. A simple example would be an employee of a company that purchases an AP on his own, brings it to the company, and connects his devices to it. The company has no idea that they have a new security issue within their networks. It doesn't necessarily have to be with malicious intent, however, if someone finds access to this AP, he has access to the corporate network. Although, it is not that easy anymore to break into an AP nowadays, but once it is installed, there is still the chance of someone breaking into it, and ultimately in your system.
A wireless evil twin represents a more sinister type of rogue APs since it's designed to look like a normal AP that is already on your network. As you can picture, it's not. It has a similar SSID name or almost the same configurations which makes it hard to differentiate. Here, the intent is purely malicious, and the attacker tries to get the user to connect to their AP. Once the user connects, the evil twin can become the primary AP on the network. A perfect example is WiFi hotspots. How many times have you connected to public WiFi, having nothing on your mind apart from establishing a proper connection to send messages? However, a well-placed Evil Twin can fool you very quickly. This can be prevented by using a VPN or connecting to websites via HTTPS.
Wireless Jamming
This is a type of Denial of Service, meaning it disrupts the wireless network by decreasing the "signal-to-noise ratio". The signal-to-noise ratio describes the relationship between the good signal received by the device and the rest of the signals. As long as the good part of the signal is received above the other noise, then the signal can continue. If this is not the case, the ratio is decreased and the device cannot connect or communicate over the network. This is not necessarily with malicious intent. Picture yourself using a microwave, and it's sending interference that causes the signal not to be received. Hackers can maliciously send noise over a network which ultimately creates conflict in the network. Various techniques can be used to create this noise, like sending constant random amounts of information over the network to overwhelm the signal or sending too much traffic, which uses the whole bandwidth of the network. For the attack to happen, the jamming device needs to be somewhere close, meaning the attacker needs to be close or he has to install a device somewhere in that area.
Threat Hunting
Threat Hunting is the process of identifying potential threats on the network. The goal here is to find these threats, and subsequently isolate them so that they don't represent a threat to your system or any other system. It is a constant process that is used over various systems. The biggest problem here is that you can only react after the attack already happened. The goal is to prevent the attack from occurring and to speed up the reaction time. You have to imagine that there is a huge data amount to sift through, which makes it very hard to properly detect these threats and subsequently, react. By putting all the data in a database, threat hunters use data analytics to filter and pick out the important pieces of data that can give them specific insights.
