VPN explained

I remember exactly when I was sitting at a table with my friends, and one of them asked me if I could explain what a VPN is. Of course, they asked me, because I was the one studying Computer Science. This was many years ago, and I gave him a very vague answer, adding that I am still researching "all those" topics, and I would go back to him. You can imagine, that I did in fact, not go back to him. That really bothered me. I was curious myself and I really wanted to give him a proper explanation, but I wasn't able to.
This was one of those moments where I realized, it is just not enough to go to class, finish up your homework, and go out with your friends. If I want to be able to explain those things to other people and expand my knowledge in the IT sector, concerning topics that actually interest me, I would have to actually sit down and do my own research in my free time.
Therefore, in this blog post, I am going to explain what a VPN is. Not for just telling your friends that you know what it is or how it works, but for your own understanding. So you actually know what you are doing online, and how the different concepts work, so you know why it is being used and especially, for what reason.
What is a VPN?
VPN is the acronym for Virtual Private Network. In general, it is used to do the following things:
- It ensures that your location stays private
- Your data is encrypted
- Bypass geographical restrictions
- Surf the web anonymously
- Protection against hackers or other malicious entities
- Secure browsing on public networks
In the beginning, VPNs were only used for businesses to secure their data. Many employees work remotely, and since you're working with sensitive data that is critical for the company's business, they needed to secure the connection to avoid any harmful interception. VPN was the perfect software since it ensured privacy online and your data is encrypted.
How does it work?
So normally, what you're doing is, you type in a website domain name on the browser. Then, your data is sent automatically to the internet until it reaches a server. The server gives back the information that you requested. But, due to your request, the server has access to specific data of yours, such as your IP address, and many more information. The problem here is, that hackers can intercept and get ahold of your information. The following diagram should give you an idea of what that looks like:
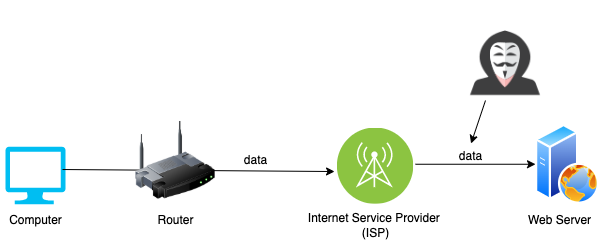
However, if you use a VPN, you create a tunnel that encrypts your information. This tunnel makes it harder for hackers to "get in" and intercept the exchange of data between you and the server. It is important to notice that it makes it harder for attackers, but it is still possible.
VPN has an extra server:
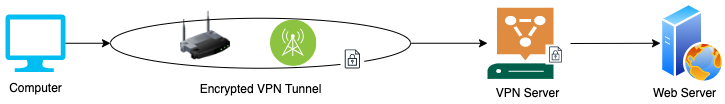
A relatable example of the proper use of a VPN would be the use of Netflix, using a VPN connection. Let's say you are streaming Netflix but you are located in Germany. What you can do is, use a VPN server that is located in the US. Subsequently, your personal information is sent to the VPN server in the United States, and then this server forwards your data to the Netflix website. The Netflix server looks at the incoming data and when it tries to trace it back, it looks like the information is coming from the US because the VPN server is located in that country. This tricks them into thinking that you're in a different location, but you're actually not. This is why many people use VPNs to access streaming services since they have different content in different countries.
Also, the government has permission to request your data from the website, to get your location. However, if you're using VPN, they will only reach the VPN server. They are unable to track you back to your original IP address. Depending on the VPN service provider, many use a no-logs policy, meaning it is not recorded what websites you visit.
Which VPN Protocols are there?
OpenVPN: Most commonly used VPN protocol. Supported by most VPN services and platforms. It uses OpenSSL as encryption.
IPsec/L2TP: IPsec/L2TP is used by most operating systems. It combines IPsec to encrypt data and L2TP to establish a secure connection.
Softether: Open-source application that works across different platforms and offers support to VPN protocols such as L2TP/IPsec, OpenVPN, and more.
IKEv2/IPsec: A protocol that quickly connects to and switches between networks. It is based on IPSec.
WireGuard: One of the new protocols that are gaining more popularity. It is aimed at performing better than other VPN services such as OpenVPN and IPsec, but it is still being developed.
PPTP: Point to Point Tunneling Protocol is one of the first widely used protocols, but it contains few leaks. It puts a stronger focus on speed than security and is helpful for bypassing restrictions from streaming services.
